TLS 1.3
TLS 1.3 (Transport Layer Security) is the latest version of the TLS protocol, it provides improved security, faster connection times, simplified protocol, support for 0-rtt (zero round trip times) connections.
TLS 1.3 is that the handshake process requires only one round trip between the client and server, the earlier versions required two round trips to complete the hand shake.
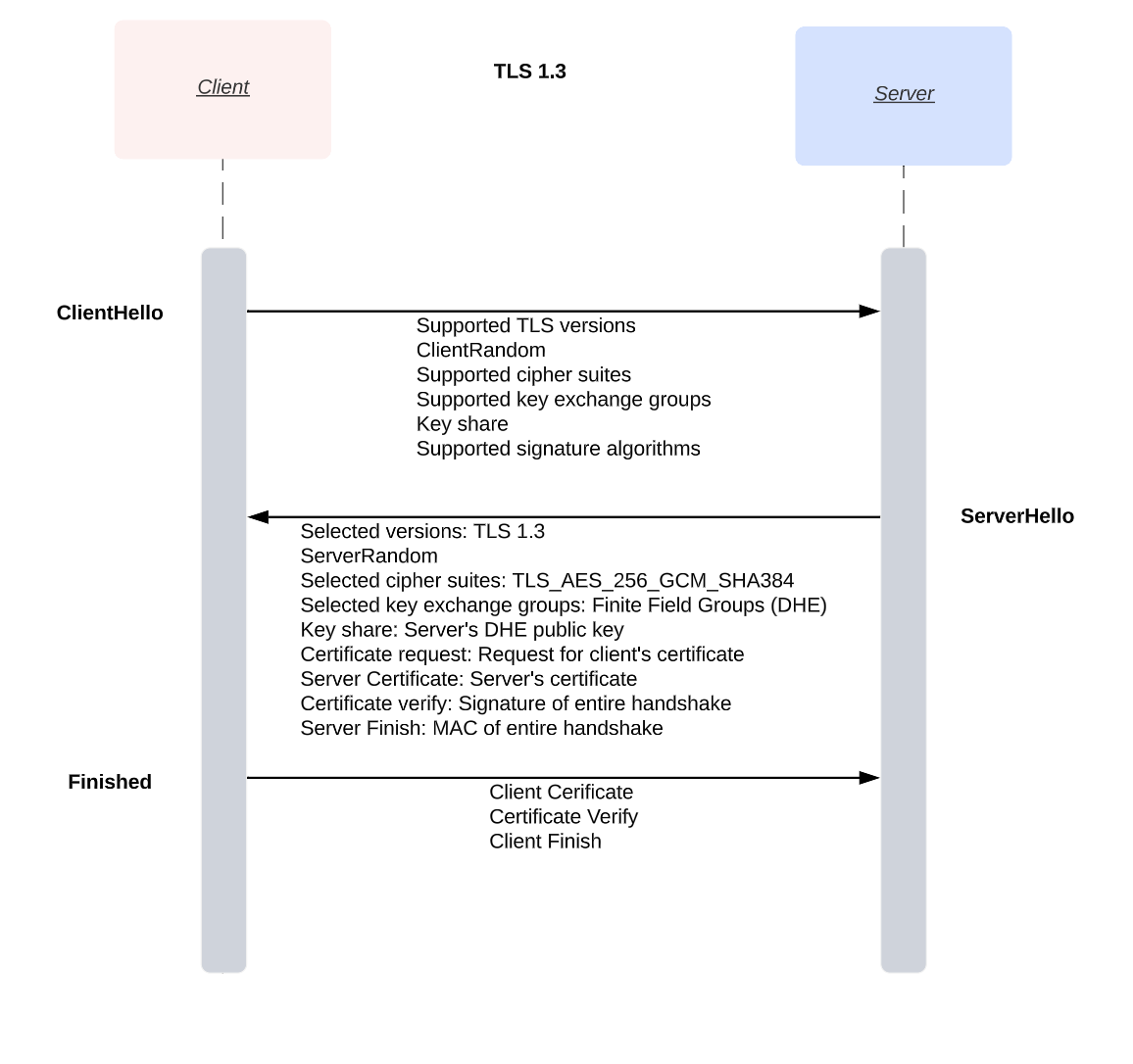
Full Handshake
- ClientHello: The client initiates the handshake by sending a
ClientHellomessage to the server. This message contains the protocol version (TLS 1.3), a list of supported cipher suites, a supported key exchange group (DHE/EC-DHE), signature algorithms, aClientRandomvalue, and optionally, thekey_shareextension containing the client's ephemeral public key for key agreement. - ServerHello: The server responds with a
ServerHellomessage, selecting the protocol version (TLS 1.3), the cipher suite to be used, seleted key exchange group, aServerRandomvalue, and thekey_shareextension containing the server's ephemeral public key for key agreement. The server also provides its certificate and proves possession of the private key associated with the certificate through aCertificateVerifymessage. - Server Parameters: The server sends additional parameters, like the
EncryptedExtensionsmessage, which may include additional information or settings required for the connection. If the server requires client authentication, it will send aCertificateRequestmessage, asking the client to provide a certificate and proof of its private key possession. - Key Derivation: Both the client and the server derive a shared secret using their respective private keys and the other party's public key from the
key_shareextension. This shared secret, along with the ClientRandom and ServerRandom values, is used to generate the necessarysymmetric keysfor encryption and message authentication. - Client Certificate and Verification: If the server requested client authentication, the client sends its certificate and a
CertificateVerifymessage to prove possession of the private key associated with the certificate. - Finished Messages: Both the client and server exchange
Finishedmessages, which are encrypted and authenticated using the previously derived symmetric keys.
How to check using cURL?
> curl --tlsv1.3 https://www.google.com -v
* Trying 172.217.16.196:443...
* Connected to www.google.com (172.217.16.196) port 443 (#0)
* ALPN: offers h2,http/1.1
* TLSv1.3 (OUT), TLS handshake, Client hello (1):
* TLSv1.3 (IN), TLS handshake, Server hello (2):
* TLSv1.3 (IN), TLS handshake, Encrypted Extensions (8):
* TLSv1.3 (IN), TLS handshake, Certificate (11):
* TLSv1.3 (IN), TLS handshake, CERT verify (15):
* TLSv1.3 (IN), TLS handshake, Finished (20):
* TLSv1.3 (OUT), TLS change cipher, Change cipher spec (1):
* TLSv1.3 (OUT), TLS handshake, Finished (20):
* SSL connection using TLSv1.3 / TLS_AES_256_GCM_SHA384
* ALPN: server accepted h2
* Server certificate:
* subject: CN=www.google.com
* start date: Mar 28 16:54:58 2023 GMT
* expire date: Jun 20 16:54:57 2023 GMT
* subjectAltName: host "www.google.com" matched cert's "www.google.com"
* issuer: C=US; O=Google Trust Services LLC; CN=GTS CA 1C3
* SSL certificate verify ok.
* using HTTP/2
* h2h3 [:method: GET]
* h2h3 [:path: /]
* h2h3 [:scheme: https]
* h2h3 [:authority: www.google.com]
* h2h3 [user-agent: curl/8.0.1]
* h2h3 [accept: */*]
* Using Stream ID: 1 (easy handle 0x133812600)
> GET / HTTP/2
> Host: www.google.com
> user-agent: curl/8.0.1
> accept: */*
>
* TLSv1.3 (IN), TLS handshake, Newsession Ticket (4):
* TLSv1.3 (IN), TLS handshake, Newsession Ticket (4):
* old SSL session ID is stale, removing
< HTTP/2 200
< date: Sun, 16 Apr 2023 16:16:59 GMT
< expires: -1
< cache-control: private, max-age=0
< content-type: text/html; charset=ISO-8859-1
< content-security-policy-report-only: object-src 'none';base-uri 'self';script-src 'nonce-szJTi7fUSY9c0t7LVmzgag' 'strict-dynamic' 'report-sample' 'unsafe-eval' 'unsafe-inline' https: http:;report-uri https://csp.withgoogle.com/csp/gws/other-hp
< p3p: CP="This is not a P3P policy! See g.co/p3phelp for more info."
< server: gws
< x-xss-protection: 0
< x-frame-options: SAMEORIGIN
< set-cookie: SOCS=CAAaBgiA9eyhBg; expires=Wed, 15-May-2024 16:16:59 GMT; path=/; domain=.google.com; Secure; SameSite=lax
< set-cookie: AEC=AUEFqZeU-LgDLXDKlQdfpSp_LdzEQ1ga6hztWTg79WslNopDmsGz8AJuHig; expires=Fri, 13-Oct-2023 16:16:59 GMT; path=/; domain=.google.com; Secure; HttpOnly; SameSite=lax
< set-cookie: __Secure-ENID=11.SE=GL_asCMotYI86NO8sixVdb-FhRJDGsUQkf_hxlDMLJmwBWeJhvHhBTgqbYhl5-7BtQAWodfjBJSPC1z13fAmNJuhsRJdx8UrYE2BCN4QWcIqDgPiIEhFObj1_k7_qNhIQdY1_QpM7z3WF-TZwvwQbanmK29Uodtb9MwX7cQrgWA; expires=Thu, 16-May-2024 08:35:17 GMT; path=/; domain=.google.com; Secure; HttpOnly; SameSite=lax
< set-cookie: CONSENT=PENDING+508; expires=Tue, 15-Apr-2025 16:16:59 GMT; path=/; domain=.google.com; Secure
< alt-svc: h3=":443"; ma=2592000,h3-29=":443"; ma=2592000
< accept-ranges: none
< vary: Accept-Encoding
<
<!doctype html>.............. .... ... .. .